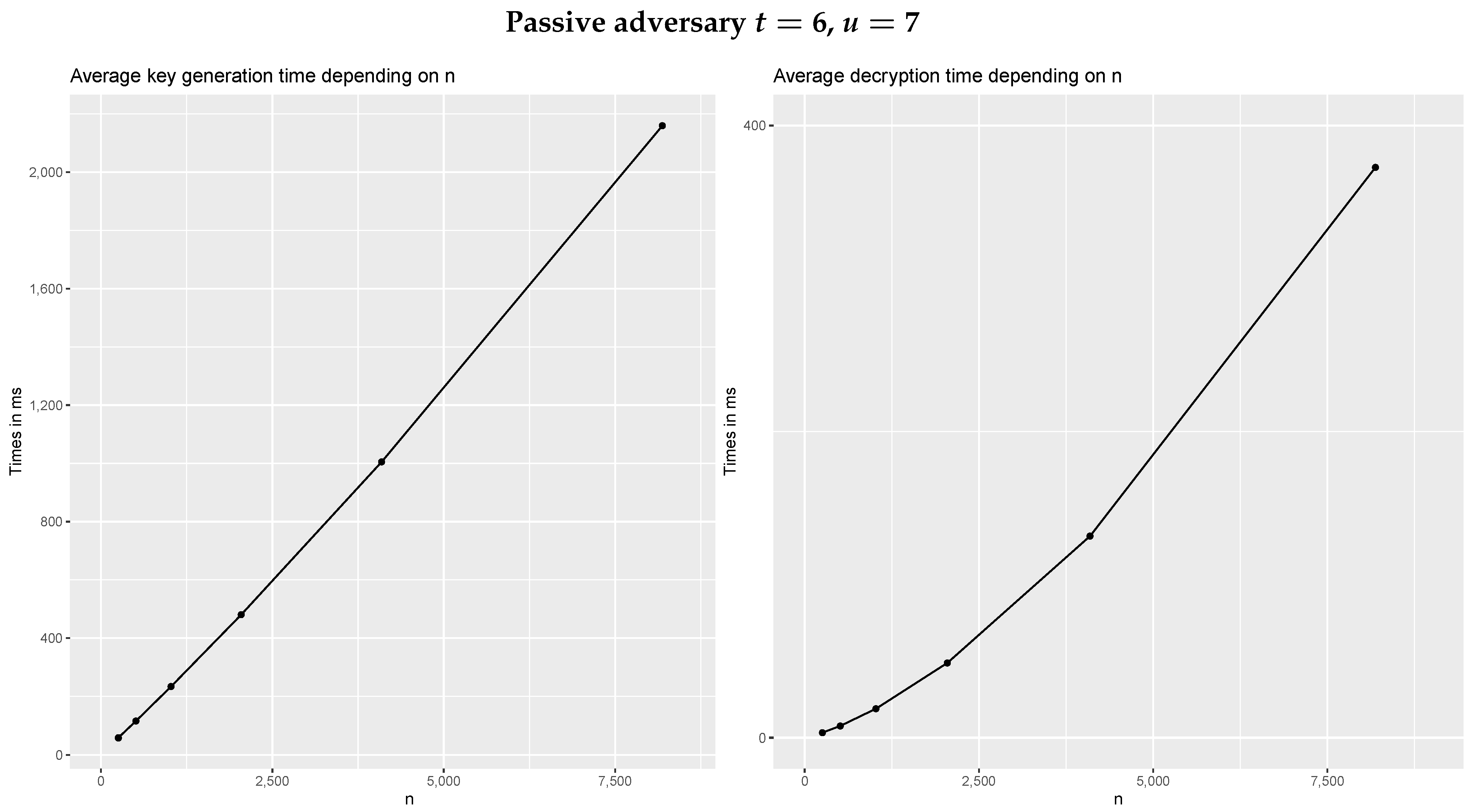
![PDF] Distributed key generation protocol with hierarchical threshold access structure | Semantic Scholar PDF] Distributed key generation protocol with hierarchical threshold access structure | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5f059b03ddd2476d996b47e7420403e2bff04e5a/6-Table1-1.png)
PDF] Distributed key generation protocol with hierarchical threshold access structure | Semantic Scholar

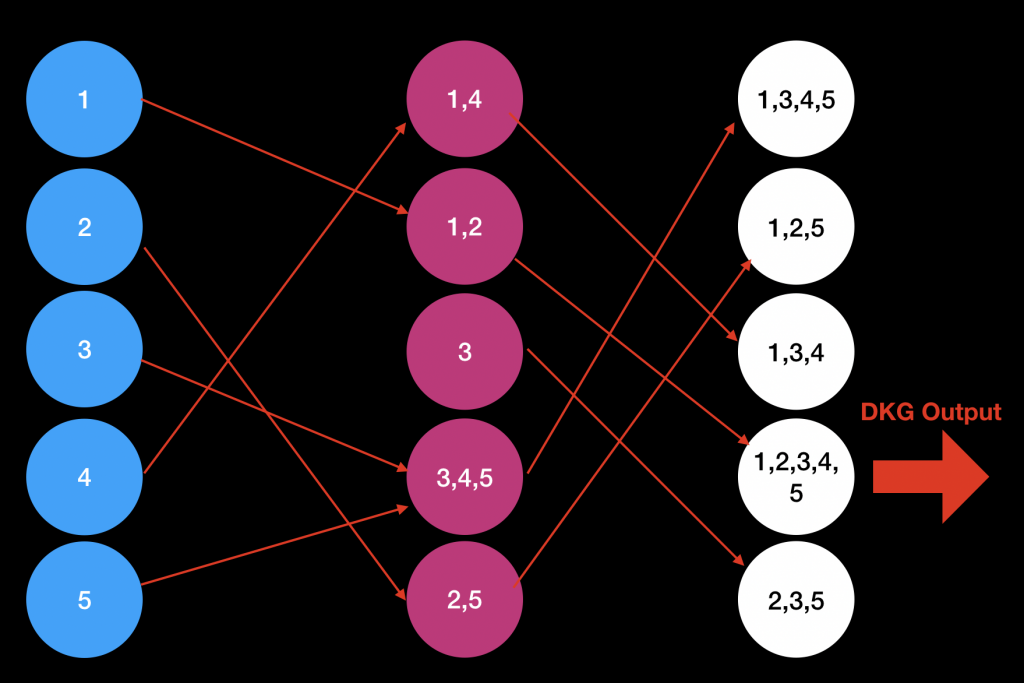
Distributed Key Generation, Threshold Signatures, BLS Scheme, NONinteractive Consensus - Clever Solution

Distributed Key Generation, Threshold Signatures, BLS Scheme, NONinteractive Consensus - Clever Solution